
FEDERAL DEVELOPMENTS
FTC Implements Broad Definition of Biometric Information; Increases Focus on Data Protection Impact Assessments
While States like Illinois, Texas, and Washington focused on opt-in consent; the FTC is focused on clear and conspicuous disclosures and accounting and planning for foreseeable harms related to the collection of biometric information.
On May 18, 2023, the Federal Trade Commission (the “FTC”) released a new policy statement on biometric information, which set forth a clear indication that the FTC will focus its Section 5 FTC Act enforcement authority over those businesses collecting or using biometric information in deceptive or unfair manners.
Regulating biometric information collection and use is not uncommon in the United States, as Illinois, Texas, and Washington all have laws requiring prior opt-in consent before collecting an individual’s biometric information. Major cities such as New York City and Baltimore have also passed local ordinances on biometric information collection and use.
In Illinois specifically, litigation has increased, with the first Biometric Information Protection Act (“BIPA”) trial resulting in a $228 million judgement. In February, the Illinois Supreme Court also determined that BIPA claims accrue each time a business collects a single data point that falls under the biometric information category (e.g., each time some’s fingerprint is scanned).
Even the new, broad omnibus U.S. state data protection laws that have proliferated in the absence of federal government action on the collection of personal information generally, have implemented the idea of “sensitive information,” which includes biometric information. Depending on the state, the collection and use of sensitive personal information requires prior opt-in consent and/or providing an individual the ability to opt-out of the collection and use of their sensitive personal information.
Now though, the FTC appears poised to increase its investigatory and enforcement activity related to unfair and deceptive business practices by leveraging a broad definition of what it considers to be biometric information and what it considers to be “significant concerns with respect to consumer privacy, data security, and the potential for bias and discrimination.”
Definition of Biometric Information
U.S. state laws, such as in Illinois, traditionally set forth a narrow scope of what they considered to be biometric information. Specifically, the U.S. state laws have focused on a sub-set of “biometric identifiers” such as retina or iris scans, finger or handprints, voiceprints, or scans of an individual’s facial geometry. Additionally, the identifiers would need to be used in a manner that is intended to identify the specific individual.
The FTC, however, in its latest policy statement makes clear it is focused on a larger swath of identifiers and information related to biometric identifiers.
The FTC defines “biometric information” as “data that depict or describe physical, biological, or behavioral traits, characteristics, or measurements of or relating to an identified or identifiable person’s body.” The policy statement also includes a non-exhaustive list of what have becomes traditional biometric information examples: (i) facial geometry and features; (ii) iris or retinas; (iii) finger or handprints; (iv) voiceprints; or (v) genetics.
However, the policy statement also gives examples of what is considered “biometric information” that go far beyond what traditional biometric information laws previously identified, such as, an individual’s characteristic movements or gestures (e.g., gait, typing patterns, etc.). Further broadening the definition of is that the FTC considers any data derived from depictions, images, descriptions, or recordings of an individual’s biometric information to also be biometric information—meaning the output form analyzing an individual’s biometric information would be considered biometric information.
Another example of how broadly the FTC’s definition of biometric information reaches is that it would also include an individual’s typing patterns. Tools analyzing typing patterns have become more and more common in the employer-employee relationship during the post COVID-19 pandemic work from home era as a tool for employers to measure productivity. Under the FTC’s policy statement, such tools would be subject to biometric information considerations. This will increase the need for employers to consider what is and is not biometric information when crafting employee and job applicant privacy notices.
FTC Authority; Specific Biometric Information Considerations
Generally, under the Federal Trade Commission Act (the “FTC Act”), the FTC has broad investigatory and enforcement power aimed at protecting consumers from unfair and/or deceptive business practices.
Under the FTC Act, a practice is unfair if it (1) causes or is likely to cause substantial injury to consumers; (2) the harm is not reasonably avoidable by consumers; and (3) the harm is not outweighed by countervailing benefits to consumers or competition. Although violations of the law may be relevant, the existence or substantial likelihood of injury is the key determination, not the illegality of the act.
The deceptive prong of the FTC’s investigatory and enforcement powers is more straight forward and typically involves a business publicly committing to one thing, but not following through on such commitment(s). For example, where a privacy notice promises to delete all data after a certain period of time, but where the data is actual kept far beyond that time period.
Regarding biometric information, the FTC policy statement sets for a “non-exhaustive” list of practices the FTC will scrutinize.
“Deception” in the biometric information space—according to the FTC includes “false or unsubstantiated marketing claims relating to the validity, reliability, accuracy, performance, fairness, or efficacy of technologies using biometric information.” Deception can also include other “deceptive” statements a business (whether they are the technology provider or user) makes about the collection or use of biometric information.
The last point is crucial, as the FTC will be looking to both the providers of biometric information technologies and the businesses that use such services.
“Unfairness” under the policy statement includes activity whereby a business:
- fails to assess foreseeable harms to consumers before collecting biometric information;
- fails to promptly address known or foreseeable risks;
- engages in surreptitious and unexpected collection or use of biometric information;
- fails to evaluate the practices and capabilities or third parties;
- fails to provide appropriate training for employees and contractors; or
- fails to conduct ongoing monitoring of technologies that the business develops, offers for sale, or uses in connection with biometric information.
Considerations for Businesses Moving Forward
Even before the FTC put out its latest policy statement—with class actions growing exponentially in states like Illinois—businesses needed to closely scrutinize their biometric information collection and use practices.
The FTC policy statement now puts forth examples of how businesses should be analyzing such practices. For example, businesses should incorporate discussions and reviews of any foreseeable harms that could come from the misuse of the in-scope biometric information and conduct on going due diligence of any current or new biometric information service providers.
Businesses that collect and use biometric information also need to ensure they have clear public-facing (e.g., to employees or consumers depending on those identified by the technologies) notices that are accurate to the biometric information practices and that clearly set forth how that information is used.
Click Here for the Original Article
Approaching Deadline to Comply with In-Person Review of Employee I-9 Documentation
Since March 2020, the federal Department of Homeland Security (DHS) has permitted employers the flexibility to engage in remote review of certain new employees’ proof of their identity and authorization to work in the United States. At the end of July 2023, those flexibility rules will sunset – although businesses will have until the end of August to fully comply. Beginning in August, DHS and its Immigration and Customs Enforcement (ICE) office will require all employees, including those hired during the pandemic, be subject to in-person review of their supporting documentation. Therefore, employers that have not been conducting in-person review of required I-9 documents must act immediately to do so.
Under pre-pandemic rules, DHS required employers to inspect each new hire’s identification and employment verification documents in-person no later than three business days following the employee’s first day of work. Employers could work with an authorized representative to assist in this review for remote workers. Such representatives could include attorneys, notaries, other remote staff, and others – including even the family or neighbors of the new hire – provided that the employer was comfortable assuming the liability associated with the representatives’ review.
Beginning in March 2020, DHS instituted exceptions for employees working exclusively in a remote setting due to COVID-19, allowing businesses to be deemed compliant with I-9 inspection requirements provided that they (1) conducted a remote review of employee documents and (2) inspected the documents in-person upon a return to normal business operations. DHS stated that employers availing themselves of this option should provide written documentation of their applicable remote onboarding and telework policies for each affected employee. DHS also instructed that, when the in-person examination of documentation occurred, employers should note the review date on the employee’s I-9. This flexibility has remained in place for all those who did not report to a company location on a regular, consistent, or predictable basis.
DHS extended its flexible rules multiple times throughout the pandemic but they now are scheduled expire at the end of July. Reflecting the way business has changed since the pandemic, though, DHS also has published a Notice of Proposed Rulemaking for a permanent remote procedure for review of immigration documents. In May 2023, however, the agency stated that, while its proposed rules for remote inspection remain pending, it did not intend to extend the pandemic era flexibility rules again. Instead, it will give employers an additional 30 days – until August 30, 2023 – to achieve compliance with regard to all hires made since the beginning of the pandemic and to institute a practice by which all new employees will have their documentation reviewed in-person once again. Therefore, employers who have not conducted in-person reviews of employees’ documents should move quickly to establish such a program as soon as possible. To do so, employers may either require employees to report to a company location to have their documentation reviewed or work with an authorized agent to have documents inspected in a location more convenient to the employee. Employers should also continue to monitor DHS pronouncements concerning enforcement of its traditional rules and the possibility of instituting flexible rules on a permanent basis in the future.
Click Here for the Original Article
CFPB Opines That Companies Using Automated Worker Surveillance Tools Must Comply with FCRA
Do companies that use workplace surveillance tools to make hiring and firing decisions risk violating the Fair Credit Reporting Act (FCRA)? According to the Consumer Financial Protection Bureau (CFPB or Bureau) in a recent comment, the answer to that question is yes. The Bureau’s official comment comes in response to a request for information issued by the White House’s Office of Science and Technology Policy on the impact of automated tools used by employers to monitor and evaluate workers. The CFPB’s position that the FCRA applies to automated worker surveillance tools is consistent with the Bureau’s March 2023 request for information on data brokers, discussed here, to determine whether the FCRA applies to modern data surveillance practices.
As background, the FCRA provides protections related to consumer reports. The FCRA defines “consumer report” to include “any written, oral, or other communication of any information by a consumer reporting agency bearing on a consumer’s credit worthiness, credit standing, credit capacity, character, general reputation, personal characteristics, or mode of living which is used or expected to be used or collected in whole or in part for the purpose of serving as a factor in establishing the consumer’s eligibility for … employment purposes.”
The gathering and use of information from worker surveillance technologies to support retention and promotion decisions has greatly increased in recent years, in large part because of COVID-19 work-from-home arrangements. But in a now-familiar refrain, the CFPB cautions that such “automated technologies may produce incomplete or inaccurate information or exacerbate biases.”
The CFPB makes clear that the FCRA may apply to worker surveillance when making decisions including hiring, firing, promotion, reassignment, retention, and compensation. The CFPB also expressed interest in exploring how the information employers obtain about their employees through such technologies can find its way into the data broker market as well as when such information is used for employment background screening and other decisions that could impact consumers.
Furthermore, the CFPB expressed significant concerns about whether entities offering evolving worker surveillance technologies to employers are complying with applicable law. The CFPB stated that a company’s choice to use new technologies does not absolve it from its legal obligations.
Our Take:
The CFPB presumably is not going to transform itself into an employment regulator, but its public announcement does signal an interest in protecting employee rights from the types of monitoring discussed by the Bureau in its comment. We expect the Bureau to consider enforcement action on this subject if a company engaged in such practices comes to its attention, which means that employers should consider their use of such technologies to ensure that they are in a defensible position. The subject matter of the Bureau’s statements lies at the intersection of employment, privacy and consumer protection laws, and we believe that all three need to be taken into account in assessing this issue. That’s why the three of us — representatives of Troutman Pepper’s Labor & Employment, Privacy, and Consumer Financial Services groups — wanted to write on this jointly and will be watching this issue together for further developments.
Click Here for the Original Article
STATE, CITY, COUNTY AND MUNICIPAL DEVELOPMENTS
U.S. Biometric Laws & Pending Legislation Tracker
The enactment of biometric privacy laws is a growing trend across the country. Existing legislation has led to a boon of class action litigation against employers, consumer-facing businesses, and technology companies for claimed violations of biometric privacy rights. It is therefore imperative that businesses remain informed of their obligations, which are increasingly expanding and being required in new jurisdictions, as non-compliance can create significant monetary exposure.
Biometric privacy laws and regulations generally require businesses to track, inform employees or consumers of, and provide methods for employees or consumers to consent to, the collection of biometric information or biometric identifiers. BCLP has been tracking enacted biometric privacy laws and proposed legislation across the United States. Below is a high-level summary of existing laws and proposed bills introduced across the country that pertain to private sector companies’ collection or use of biometric data. Additional privacy, data-breach, industry-specific, and public-sector regulations and proposed legislation exist. Readers are thus encouraged to consult their regular Bryan Cave Leighton Paisner contact or the authors of this article for more information and guidance.
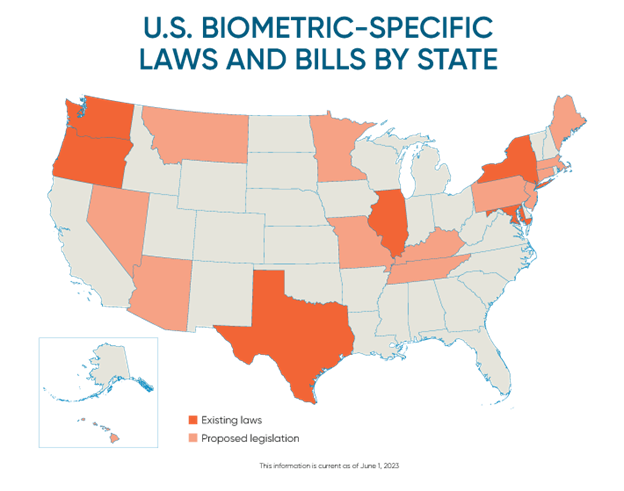
EXISTING LEGISLATION
Illinois
Biometric Information Privacy Act (“BIPA”)
740 ILCS 14/1 et seq.
Depending on whether a private entity is possessing, capturing, collecting, otherwise obtaining, or disclosing biometric information or biometric identifiers, requires: (1) a written policy, made available to the public, establishing a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information; (2) compliance with that policy; (3) protection of the biometric information using the reasonable standard of care within the industry or in a manner as protective as the entity protects other confidential and sensitive information; (4) informing the subject whose biometric information is to be collected of the specific purposes and length of term for which biometric information is being collected, stored, or used; and (5) receiving a written release from the individual to proceed with the collection or disclosure of the biometric information. Provides for recovery of liquidated statutory damages or actual damages, and attorneys’ fees and expenses. (But see Proposed Legislation).
Maryland
Labor and Employment Code § 3-717
Prohibits employers from using facial recognition service for purpose of creating a facial template during applicant interview for employment, unless applicant consents.
New York
N.Y. LAB. LAW § 201-aA
Prohibits employers from requiring a fingerprint from employees, as a condition of securing employment or of continuing employment, unless as provided by other laws. (See also New York State Department of Labor RO-10-0024 for opinion on use of a biometric device in a time clock).
New York City, New York
City of New York Administrative Code, Title 22, Chapter 12.
Any “commercial establishment” that collects biometric information from “customers” must disclose the collection “by placing a clear and conspicuous sign near all of the commercial establishment’s customer entrances.” Makes it unlawful to sell, lease, trade, share, exchange for anything of value, or otherwise profit from the transaction of biometric identifier information. Provides for recovery of damages to prevailing party.
Oregon
Portland City Code, Title 34- Digital Justice, Chapters 34.10.010-34.10-050.
Prohibits the use of Facial Recognition Technologies in Places of Public Accommodation by Private Entities within the boundaries of the City of Portland. Provides for recovery of damages sustained as a result of the violation of $1,000 per day for each day of violation, whichever is greater.
Texas
TEX. BUS. & COM. CODE ANN. § 503.001
Requires that a person capturing a biometric identifier of an individual for a commercial purpose inform the individual before capturing the biometric identifier and receive the individual’s consent and requires protecting the data from disclosure using reasonable care and in a manner as protective as the entity protects other confidential information. Biometric identifiers must be destroyed within a reasonable time, but not later than the first anniversary of the date the purpose for collecting the biometric identifier expires. Also prohibits a person in possession of a biometric identifier of an individual from selling, leasing, or otherwise disclosing the biometric identifier unless in certain circumstances. Provides for a civil penalty of no more than $25,000 for each violation, enforceable by the Texas Attorney General.
Washington
WASH. REV. CODE §§ 19.375.010 et seq.
Provides that a person may not enroll a biometric identifier in a database for a commercial purpose, without first providing notice, obtaining consent, or providing a mechanism to prevent the subsequent use of a biometric identifier for a commercial purpose. Provides for enforcement by the Texas Attorney General under the Washington Consumer Protection Act.
My Health My Data Act (effective March 31, 2024)
“Biometric data” included in the broad definition of “consumer health data.”
Read our insight on this topic.
PROPOSED LEGISLATION
Arizona
2023 AZ S.B. 1238[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater.
Connecticut
2023 CT S.B. 730[Similar to NYC Ordinance] Would require that any entity using facial recognition technology to identify customers and guests in a public space post a clear disclosure of such use.
Hawaii
2023 HI H.B. 1085[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater.
Illinois
2023 IL H.B. 1230
Would amend the BIPA to provide to carve out application to health care employers who biometric information or biometric identifiers for employment, human resources, compliance, payroll, identification, authentication, safety, security, or fraud prevention purposes.
2023 IL S.B. 1511
2023 IL H.B. 2259
2023 IL H.B. 4102
Would amend the BIPA to allow collection of biometric information for a “security purpose” (preventing theft, fraud, trespass, controlling access to property).
2023 IL S.B. 1506
2023 IL H.B. 2335
Would amend the BIPA to exclude information converted to a mathematical representation from definition of “biometric identifier” (or devices that so convert a person’s biometric identifier or information to a mathematical representation). Would also clarify that if biometric identifier or information is captured for same repeated process, obtaining informed consent is only required at initial collection. Would also not require consent if information collected for “security purpose.” Would also amend the Workers’ Compensation Act to state that it does not preempt an employee’s BIPA claim.
2023 IL H.B. 3199
2023 IL H.B. 2252
Would amend the BIPA to exclude information “that cannot be used to create the original biometric identifier” from definition of “biometric information.” Would also change term “written release” to “written consent” and clarify that consent can be obtained electronically. Would also provide for 1-year statute of limitations and 30 day notice period/opportunity to cure for violations. Would eliminate statutory damages. Would also clarify that BIPA does not apply to private entity whose employees are covered by collective bargaining agreement that provides for different policies regarding biometric information.
2023 IL H.B. 3204
Would amend the BIPA to provide for 1-year statute of limitations.
2023 IL H.B. 3811
Would amend the BIPA to provide for a single damages recovery (rather than “per scan”), but increase potential liquidated statutory damages to $1500 per person.
Kentucky
2023 KY S.B. 239
2023 KY H.B. 483[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater. Also provides for Attorney General enforcement.
Maine
Act to Give Consumers Control Over Sensitive Personal Data
2023 ME H.P. 1094[Similar to Illinois BIPA + Consumer Privacy statutes] Would require a private entity in possession of non-employees’ biometric identifiers information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying non-employees’ biometric identifiers. Would also require affirmative written consent prior to collection or disclosure of biometric identifier. Would require, upon request, disclosure of certain information to individual whose biometric information is collected or possessed. Would also grant right to request destruction of biometric identifiers. Would prohibit private entity from retaining a biometric identifier of employee for purpose of employee tracking. Would also prohibit discrimination based on refusal to provide affirmative written consent to providing biometric identifier. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater. Also provides for Attorney General enforcement.
Maryland
2023 MD S.B. 169
2023 MD H.B. 33
Would require a private entity in possession of non-employees’ biometric identifiers information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying non-employees’ biometric identifiers. Would also require affirmative written consent prior to collection or disclosure of biometric identifier. Would require, upon request, disclosure of certain information to individual whose biometric information is collected or possessed. Would also grant right to request destruction of biometric identifiers. Would prohibit private entity from retaining a biometric identifier of employee for purpose of employee tracking. Would also prohibit discrimination based on refusal to provide affirmative written consent to providing biometric identifier. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater. Also provides for Attorney General enforcement.
Massachusetts
Biometric Information Privacy Act
2023 MA S.B. 195[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for Attorney General enforcement or private right of action to recover statutory damages of at least $5,000 per violation or actual damages, whichever is greater.
2023 MA H.D. 3053
2023 MA H.B. 63
Would require a “covered entity” or “data processor” to obtain informed, handwritten/non-electronic consent to collection and processing of biometric information for a specific purpose, excluding monetization. Would also require having a “Biometric Privacy Policy.” Would also impose annual reporting and data security requirements.
Minnesota
2023 MN S.F. 954
2023 MN H.F. 2532[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater.
Missouri
Biometric Information Privacy Act
2023 MO H.B. 1047
2023 MO H.B. 1225
Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Would prohibit conditioning provision of goods or services on collection, use, disclosure of a biometric identifier unless “strictly necessary” to provide the good or service. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater.
Montana
Genetic Information Privacy Act
2023 MT S.B. 351
Would require that “genetic data of Montana residents or biometric data collected in the state” be stored “within the territorial boundaries of the United States.” “Biometric data” is not defined. Violations subject to Attorney General enforcement.
Nevada
2023 NV S.B. 370[Similar to Illinois BIPA] Would require a private entity in possession of a biometric identifier to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers. Violation would be “deceptive trade practice” subject to Deceptive Trade Practices Act.
New Jersey
2022 NJ S.B. 3499
Would prohibit use of facial recognition technology on consumer at any retail location or “place of public accommodation,” except for a “legitimate safety purpose.” Violation would be an “unlawful practice” under Consumer Fraud Act punishable by monetary penalty. Violations also subject to Attorney General enforcement and assessment of punitive and treble damages.
New York
Biometric Privacy Act
2023 NY A.B 1362
2023 NY S.B. 4457[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater.
2023 NY S.B. 2390
Would prohibit a private entity from using biometric identifiers or biometric information for any advertising or marketing activity intended to be used to influence business volume, sales, or market share, or to evaluate effectiveness of marketing practices or personnel.
2023 NY A.B. 7625
Would prohibit use of “biometric surveillance system” in place of public accommodation. Would also require informed written consent prior to collection of biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater.
Pennsylvania
Biometric Identifier Signage Act
2023 PA H.B. 926[Similar to NYC Ordinance] Would require any “commercial establishment” (retail store, restaurant, hotel, motel, place of entertainment) that collects, retains, converts, stores, or shares biometric identifier information of customers to post a clear and conspicuous notice disclosing use of the technology. Would prohibit the sale, trade, sharing, or profiting from transactions of biometric identifier information. Violations subject to private right of action to recover statutory damages.
Tennessee
Consumer Biometric Data Protection Act
2023 TN S.B. 339
2023 TN H.B. 932[Similar to Illinois BIPA] Would require a private entity in possession of biometric identifiers or biometric information to develop a written policy, and establish a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information. Would also require informed written consent prior to collection of biometric identifiers or biometric information. Provides for recovery of liquidated statutory damages or actual damages, whichever is greater. Violation would be “unfair or deceptive act or practice” subject to penalties under Consumer Protection Act of 1977.
Texas
2023 TX H.B. 4849[Similar to NYC Ordinance] Would require a business using facial recognition technology for purpose of identifying a customer or guest in a space generally accessible to the public to post a clear and conspicuous notice disclosing use of the technology.
Biometric Data Privacy Act of 2023
2023 TX H.B. 4705
Would amend the Business and Commerce to add requirement that consent to collection of biometric identifier or biometric information be in writing. Would also add private right of action for violation.
Federal
Stop Spying Bosses Act
2023 S.262
Would require an employer to disclose any workplace surveillance conducted on a “covered individual” in a “conspicuous, freely accessible, and readily available” manner.
Click Here for the Original Article
New Florida law will require private employers to use E-Verify
Introduction
On 10 May 2023, Florida Governor Ron DeSantis signed into law a new immigration bill, SB 1718. While the wide-ranging bill has implications on a variety of subjects from health care, driver’s licences and human smuggling, this article will focus on its employment related implications. The new law places Florida among the 20 states that require E-Verify for some or all employees. From 1 July 2023, private employers with more than 25 employees will be required to use E-Verify for all new hires. Notably, Florida public employers and contractors have been required to use E-Verify since 1 January 2021.
What is E-Verify?
E-Verify is an online employment verification system operated by the federal government. It is not a substitute for the I-9 process, but rather an additional method of employment verification. Employers that use E-Verify transcribe the information from each I-9 into E-Verify, and the system verifies whether the information provided by the employee is accurate and whether the employee is authorised to work in the United States. Federal law does not require employers to use E-Verify, aside from certain federal contractors. Over the last decade or more, various states have implemented different requirements regarding the use of E-Verify, and employers operating in multiple states face a patchwork of laws.
What does SB-1718 require of employers?
Beginning on 1 July 2023, private employers with more than 25 employees will be required to use E-Verify to verify that newly hired employees are legally authorised to work in the United States. The employment-related provisions of SB 1718 amend existing Florida Statute 448.095. An employer may not employ anyone who is not authorised to work in the United States. Use of the E-Verify system creates a rebuttable presumption that the employer has complied with the laws on employment verification.
For purposes of SB 1718, an “employee” is defined as:
an individual filling a permanent position who performs labour or services under the control or direction of an employer that has the power or right to control and direct the employee in the material details of how the work is to be performed.
Excluded from this definition are independent contractors and individuals hired by the occupant or owner of a private residence to engage in casual labour that is performed solely in a private residence, such as house cleaning and handyman work.
If E-Verify is unavailable for three business days after the employee begins working, the employer is required to use Form I-9 to verify employment eligibility and is excused from using E-Verify. The employer must document the unavailability of E-Verify by retaining a screenshot from each day showing the employer’s inability to access the system. Employers must retain this documentation, as well as copies of the documentation provided by the employee and the results of a successful E-Verify search, for a period of at least three years.
Penalties for non-compliance
Enforcement powers are vested in the Florida Department of Law Enforcement, the Attorney General, the State Attorney, and the Florida Department of Economic Opportunity (DEO), any of which are permitted to request that employers provide verification of a new employee’s employment eligibility.
Beginning on 1 July 2024, employers are subject to penalties imposed by the DEO for non-compliance. If the DEO determines that an employer has failed to use E-Verify to verify employment eligibility as required, it will issue a determination of non-compliance that provides the employer with 30 days to cure the non-compliance. If the DEO determines that an employer failed to use E-Verify three times in any 24-month period, the employer will be subject to a fine of $1,000 per day and revocation of state licences until the non-compliance is resolved.
The DEO is further granted authority to determine whether an employer has “knowingly employed an unauthorised alien” without verifying their employment eligibility. If an employer is found to have “knowingly employed an unauthorised alien,” the employer will be required to repay any economic development incentives that it has received and will be placed on a one-year probation, which will require quarterly reporting to the DEO to demonstrate compliance.
If the employer has a subsequent violation within 24 months of the previous violation, it is subject to the suspension or revocation of all state licences, based on the number of unauthorised aliens employed, as follows:
- one to 10 unauthorised employees results in the suspension of all applicable licences for up to 30 days;
- 11 to 50 unauthorised employees results in the suspension of all applicable licences for up to 60 days; and
- more than 50 unauthorised employees results in all applicable licences being revoked.
Comment
To be ready for this new law, employers need to ensure I-9s for existing employees are compliant with existing law and need to be ready to use E-Verify for all new hires when the law goes into effect on 1 July 2023.
Click Here for the Original Article
Texas Tightens State’s Data Breach Notification Law
On May 27, 2023, Texas’ Governor signed Senate Bill 768 amending Texas’ data breach notification law. The law in question, Section 521.053 of the Texas Business and Commerce Code, sets out the specific requirements any person conducting business in the state who owns or licenses sensitive personal information in a computerized format must follow in the event of any breach of system security.
The amendment updates only the portion of the law requiring a business to notify the Texas Attorney General of any data breach affecting at least 250 Texas residents. Previously, the law required such persons to notify the Texas Attorney General within 60 days of discovering a breach affecting 250+ residents but did not specify a particular method of providing the notice. The amendment shortens the deadline from 60 days to “as soon as practicable and not later than 30 days” and requires such persons to submit the notification via an electronic form accessible on the Attorney General’s website.
The changes go into effect on September 1, 2023. However, the amendment does not disturb any of the other requirements of the law that are already in effect. Such persons are still required to provide notice of a data breach to affected individuals “without unreasonable delay” but not later than 60 days after discovering the breach. For breaches affecting more than 10,000 individuals, such persons are required to notify each consumer reporting agency without unreasonable delay. In the case of a person who maintains computerized sensitive personal information on behalf of another and experiences a breach of system security, notice must be provided to the owner or license holder of the information “immediately after discovering the breach.”
Although the amendment brings Texas’ rules more closely in line with some other states, there remains a complicated and often conflicting web of data breach rules nationwide. Connecticut, for example, imposes a 60-day requirement for notifying affected individuals (similar to Texas) but requires all data breaches to be reported to the state’s Attorney General (not only when the breach affects more than a specified number of residents). Also, Connecticut and four other jurisdictions require credit monitoring, and ID theft services be provided for a period of time at no cost to affected persons, though that is not the case in the Lone Star State. Florida, on the other hand, is both more and less strict than Texas, its law requires notifications to individuals within 30 days (stricter than Texas) but imposes a higher threshold (500 affected residents) before requiring a notification to the Attorney General. These are just a few of the nuances organizations must grapple with when facing a data breach affecting individuals in multiple states. Because Texas’ data breach law allows the business to choose to give notice under the laws where the individual is located or under Texas’ laws when a breach affects a non-resident, it can be advantageous to know the distinctions.
Click Here for the Original Article
Colorado Enacts Legislation Restricting Employers from Requesting Age-Related Information from Job Applicants
On June 2, 2023, Colorado Governor Jared Polis signed into law Senate Bill 23-058, the Job Application Fairness Act (JAFA), prohibiting employers from inquiring about a job applicant’s age during the hiring process. JAFA’s enactment adds to the requirements and proscriptions Colorado has implemented in the hiring process, including a “ban-the-box” restriction on inquiring about criminal histories and requiring the inclusion of salary and benefits information in job postings.
The specific information JAFA forbids employers from inquiring about includes an applicant’s (1) age, (2) date of birth, and (3) dates of attendance at or graduation from an educational institution. If employers request that applicants provide application materials—such as transcripts or graduation certificates—employers must notify applicants that they may redact information that identifies their age, date of birth, or dates of school attendance or graduation.
Notably, these restrictions apply only “at the time of an initial employment application,” mirroring the limitations on inquiring as to criminal histories under the Colorado Chance to Compete Act. See Colo. Rev. Stat. § 8-2-130(3)(a)(III) (limiting inquiries into an applicant’s criminal history on an initial employment application, but not later in the hiring process).
JAFA does permit employers to request that an applicant verify compliance with age requirements in an initial employment application, but only under limited circumstances where:
- Age is a bona fide occupational qualification pertaining to public or occupational safety;
- Such information is required under federal law or regulation; or
- Such information is required under a state or local law or regulation based on a bona fide occupational qualification.
These verification requests must not, however, require disclosure of an individual’s specific age, date of birth, or dates of attendance at or date of graduation from an educational institution on the initial employment application.
JAFA does not create a private cause of action, so applicants cannot bring suit for a violation of the law. An employer may, however, be subject to penalties if the Colorado Department of Labor and Employment (CDLE) finds a violation of JAFA. The law permits aggrieved applicants to file a complaint alleging a violation of JAFA within 12 months of a violation, and the CDLE will then investigate whether the complaint has merit. If the CDLE finds an employer has violated the law, the employer faces the following progressive penalties:
- First violation: Warning and order requiring compliance within 15 business days.
- Second violation: Order requiring compliance within 15 business days and a maximum civil penalty of $1,000.
- Subsequent violations: Order requiring compliance within 15 business days and a maximum civil penalty of $2,500.
Importantly, the CDLE will consider each distinct job posting that violates JAFA as a separate violation, potentially resulting in significant financial liability if the employer has systematically violated the law in multiple job postings.
JAFA becomes effective July 1, 2024, so employers have a little time to review their hiring practices to ensure compliance with its requirements. Once in effect, Colorado joins California, Connecticut, Minnesota, and Pennsylvania as states with legislation prohibiting age-related inquiries during the job application process.
Click Here for the Original Article
New York Legislature Bans Consideration of Most Older Convictions in Employment Decisions
In the final hours of the 2023 legislative session, the New York Legislature passed Assembly Bill 1029C / Senate Bill 7551A, the “Clean Slate Act.” If signed by Governor Hochul, it will provide for the automatic sealing of the records of certain convictions after specified periods of time. The measure would not take effect, however, until one year after signing. It is intended to increase employment opportunities for those with past criminal histories who have had no recent convictions. Under the bill, the State Human Rights Law would prohibit employers from inquiring about sealed records or discriminating against applicants or employees based upon sealed records.
Automatic Sealing
After taking effect this bill would immediately seal the records of criminal convictions under state law as follows:
- Misdemeanorswould be sealed three years from the individual’s release, or the imposition of sentence if there was no sentence of incarceration.
- Felonieswould be sealed after eight years from release.
Not eligible for sealing would be Class A-I felonies, the most serious category, for which a maximum sentence of life imprisonment may be imposed (e.g., murder, first-degree kidnapping, first-degree arson, and first-degree illegal narcotics possession) and convictions requiring registration as a sex offender.
Requirements for Sealing
Sealing would be automatic except where the convicted individual has a criminal charge pending or is on probation or under parole supervision when the statutory time period for automatic sealing elapses.
Discrimination Based Upon Sealed Records Prohibited
The bill would amend the New York State Human Rights law1 to prohibit employers from making any inquiry regarding or discriminating against individuals based upon automatically sealed conviction records. Records automatically sealed under this bill could still be accessed and used under these circumstances:
- As part of new criminal cases;
- By law enforcement officers conducting an investigation;
- By any entity that is required under state or federal law to conduct a fingerprint-based background check;
- By an entity authorized to conduct a fingerprint-based background check where a job applicant would be working with children, the elderly or vulnerable adults; and
- By a licensing officer processing a firearm license application.
Notably, the Clean Slate Act would only seal convictions under New York’s penal law. The Act would not seal criminal convictions under federal law or the criminal law of any state other than New York.
In anticipation of this legislation’s taking effect, employers are encouraged to review personnel practices concerning background checks and the use of conviction records. Once the law is effective it would also be advisable to consult with employment counsel prior to taking an employment action in New York State based upon an individual’s criminal history.
Littler will continue to monitor the status of the bill and any amendments or regulations that affect compliance obligations.
Footnotes
1 N.Y. Exec. L. §296(16).
Click Here for the Original Article
New Rule Will Limit DC Employers’ Ability to Crack Down on Employee Cannabis Use
DC employers will no longer be able to take adverse action against employees for certain cannabis use.
The new rules are part of the Cannabis Employment Protections Amendment Act, which was passed by the DC Council then approved by Mayor Muriel Bowser last July.
The Act is scheduled to take effect on July 13, 2023 or when it’s included in an approved budget, whichever is later. The Act is not currently included in any fiscal budget.
What Actions will be Prohibited?
The Act prohibits an employer from taking an adverse action like terminating an employee or refusing to hire a candidate based on the individual’s:
- Use of cannabis;
- Status as a medical cannabis program patient; or
- Testing positive for marijuana in an employer drug test without additional factors indicating they are impaired.
In a nutshell, an employer cannot take any adverse action against an employee or applicant based on a drug test showing cannabis in their system, unless there is some evidence to show they are impaired.
According to the new law, the bar to show impairment is high. An employer has to show that the employee manifests specific and articulable symptoms while working or during their work hours that substantially decrease or lessen their performance or that the specific articulable symptoms interfere with an employer’s obligation to provide a safe and healthy workplace as required by DC and federal occupational safety and health laws.
Will an Employer ever be Able to Take an Adverse Action Related to Cannabis Use?
Yes, an employer can still take an adverse employment action related to an employee’s use of cannabis in three situations:
- The position is designated as “safety sensitive,” which is defined in the law as one in which it is reasonably foreseeable that if the employee performs their job duties while under the influence of drugs or alcohol, they would cause actual, immediate, and serious bodily injury or loss of life to themselves or others;
- The employer’s actions are required by federal statute, regulation, contract, or funding agreement; or
- The employee used or possessed cannabis at their job, though there is an important exception for medical cannabis use.
What about Medical Cannabis Use?
Under the law, an employer has to treat a qualifying patient’s use of medical marijuana for a disability in the same manner as it would treat the legal use of a controlled substance prescribed by a health care professional, subject to narrow exceptions. Specifically, the law appears to allow employees with disabilities to use medical marijuana at work as a medical accommodation as long as 1) it is in a nonsmokeable form at an employer’s location; 2) the employee is not in a safety sensitive position; 3) the employer is not committing a violation of federal law, regulation, contract, or funding agreement; and 4) the employee cannot be “impaired” as defined above
Employers will also have to provide employees with certain notices under the law.
In anticipation of the law’s effective date, DC employers should begin assessing which positions will be covered by the law and any changes to their drug testing practices that will need to be adjusted to comply with this law.
Click Here for the Original Article
COURT CASES
Colorado’s Job Application Fairness Act Restricts Employers’ Ability to Request Age-Related Information From Applicants
On June 2, 2023, Colorado enacted the Job Application Fairness Act (JAFA), joining California, Connecticut, Minnesota, and Pennsylvania as states prohibiting employers from requesting age-related information during the hiring process. Starting on July 1, 2024, JAFA will bar Colorado employers from requesting or requiring that job applicants provide information related to “age, date of birth, or dates of attendance at or graduation from an educational institution” on initial employment applications.
Quick Hits
- Effective July 1, 2024, employers are barred from requesting applicants to provide age-related information, but are permitted to ask them to confirm whether they meet certain age restrictions.
- Penalties include warnings and compliance orders for a first violation, $1,000 for a second violation, and $2,500 for each third and subsequent violation.
While JAFA permits employers to require applicants to provide copies of certifications or transcripts “at the time of an initial employment application,” they must notify applicants that they may redact information identifying age, date of birth, and/or dates of attendance at or graduation from an educational institution. JAFA also allows employers to request that applicants verify compliance with age requirements that are required by (1) “a bona fide occupational qualification pertaining to public or occupational safety,” (2) “a federal law or regulation,” or (3) “a state or local law or regulation based on a bona fide occupational qualification.” Even so, such verification requests may not require disclosure of an individual’s specific age, date of birth, or dates of attendance at or graduation from an educational institution on an initial employment application.
Penalties for violations of JAFA increase with each subsequent violation. For a first violation, an employer may receive a warning and an order requiring compliance within fifteen business days. A second violation carries an order requiring compliance within fifteen business days as well as a civil penalty of up to $1,000, and the civil penalty increases to a maximum of $2,500 for a third and subsequent violation. For purposes of assessing penalties, “each distinct job posting violating [the statute] constitutes a separate violation.”
JAFA adds to the restrictions already placed on the types of information Colorado employers may request from applicants. Since September 1, 2021, Colorado’s Chance to Compete Act, commonly known as “ban the box” legislation, has prevented employers with eleven or more employees from stating in an advertisement for employment that a person with a criminal history may not apply. The Chance to Compete Act, similar to JAFA, further prohibits employers from inquiring into, or requiring disclosure of, an applicant’s criminal history on an initial employment application.
Colorado employers may want to review their job postings and advertisements, as well as employment applications and the corresponding hiring processes, in preparation for ensuring compliance with JAFA come summer 2024. Employers may also want to train employees involved in the hiring and interviewing process concerning JAFA’s restrictions.
Click Here for the Original Article
California Supreme Court Adopts Broader Definition of “Disclosure” Under State Whistleblower Law
In People ex rel. Garcia-Brower v. Kolla’s, Inc., the California Supreme Court resolved a split between the Courts of Appeal for the First and Second Districts over whether a protected “disclosure” under Labor Code section 1102.5(b) includes a report of unlawful activity made to an employer or agency that already knew about the reported unlawful activity. The Supreme Court held that it does.
Background
In June 2014, the Department of Labor Standards Enforcement (DLSE) filed a complaint against Kolla’s Inc., a nightclub in Orange County, California, and its owner. The DLSE alleged that after an employee complained that she was not paid for three shifts, Kolla’s owner fired her and threatened to report her to immigration authorities. Because Kolla’s and its owner refused to accept the DLSE’s proposed remedies, the Labor Commissioner sued them in Superior Court for various Labor Code violations, including retaliation in violation of section 1102.5(b).
Kolla’s and its owner did not appear in the lawsuit. Thus, the trial court entered default judgment against them on most of the Labor Commissioner’s claims. But the trial court held that the Labor Commissioner did not state a claim under Labor Code section 1102.5(b) because the employee reported her complaints to her employer rather than a government agency.
The Labor Commissioner appealed. On appeal, the Court of Appeal affirmed the trial court’s judgment on the section 1102.5(b) claim. But it did so for a different reason. In a 2-1 opinion, the Court of Appeal held a private employee’s report of unlawful activity is not a protected “disclosure” unless the employee reveals new information. According to the Court of Appeal, the employee’s report to Kolla’s owner of wrongdoing was not a protected whistleblowing activity because they already knew about their own wrongdoing.
The Court of Appeal’s decision crystalized a split between the intermediate courts regarding the meaning of “disclose” under section 1102.5(b). In 2012, the Court of Appeal, First District had also held that “disclose” under section 1102.5(b) does not include reports of information already known. But in 2014, the Court of Appeal, Second District held that section 1102.5(b) does not limit disclosures to information that is not yet known. In Kolla’s, the Supreme Court would resolve this split.
California Supreme Court Holding
The Supreme Court reversed the Court of Appeal, and held that “disclose,” as used in section 1102.5(b) includes complaints that an employer or government agency already knows about.
To start, the Supreme Court explained that “disclosure” has several plausible meanings. As shown by the split between the Courts of Appeal, “disclose” could mean to bring new information into view or it could mean bring into view information that the discloser has special access to. The Supreme Court adopted the broader definition of “disclose,” which includes the reporting of unlawful activities to an employer or agency that already knew about the violations.
According to the Supreme Court, the legislative history supported a broad definition. When the Legislature passed section 1102.5(b) in 1984, and amended it in 2003 and 2013, it used terms “report,” “inform,” and “complain” interchangeably to describe disclosures protected by the statute. Thus, the Supreme Court held that “disclose” was meant to mean “report,” inform,” or “complain,” which the Supreme Court held readily encompasses the employee’s conduct in this case. Furthermore, a bill amending section 1102.5(b) in 2013 stated that California’s public policy was to support workers “be[ing] able to report concerns without fear of retaliation or discrimination.” Moreover, in 2013, the Legislature expanded section 1102.5(b)’s coverage to prohibit retaliation by persons with authority to investigate or correct the violation. Based on this legislative history, the Supreme Court concluded that “disclose” under section 1102.5(b) includes telling an employer information that they already knew about.
The Supreme Court also held a broad definition of section 1102.5(b) supports its purpose of increasing employee protections. An employee may feel more comfortable approaching their employer regarding workplace safety hazards or wage and hour violations knowing a colleague made a similar disclosure. The Supreme Court suggested that an employer may be more likely to fix violations if multiple employees disclose the same wrongdoing. Moreover, an employee without antiretaliation protections may be hesitant to discuss a violation that they know their coworker has already disclosed. Denying protection for employees making secondary disclosures would deny employers and government agencies of corroborating information. Accordingly, the Supreme Court defined “disclose” more broadly to promote section 1102.5(b)’s purpose of enhancing employee protections.
Key Takeaway
With this new clarity, employers should continue to document all concerns raised by employees. The Supreme Court reiterated that an employer can rebut a whistleblower retaliation claim by presenting clear and convincing evidence that a legitimate non-retaliatory interest supported the employer’s decisions. Therefore, an employer can protect themselves by using best practices and documenting all instances of problematic employee behavior and employee complaints. Good documentation will provide contemporaneous evidence of legitimate non-retaliatory reasons for an action if an employer is sued. And, employers with questions concerning an employee’s complaint should consult with legal counsel to ensure an appropriate response.
Click Here for the Original Article
Pay Equity Claims Are on the Rise – How Are Courts Interpreting the Differences in State and Federal Laws?
As discussed in prior blog posts, here, here, and here, pay equity is a hot topic for employee retention and compliance. This principle of equal pay for equal work has been mandated since the Equal Pay Act of 1963 and reiterated in Title VII of the Civil Rights Act of 1964. More recently, legislators at the federal, state, and local level have increased their focus on pay equity and pay transparency initiatives. Because of this legislative activity, pay equity has also received increased attention from the Plaintiffs’ bar, and in recent years, pay equity lawsuits have been brought with increasing frequency. Against this backdrop, employers face the tough task of navigating a complex patchwork of pay equity laws in order to achieve fair and legally-compliant compensation practices, while ensuring that their compensation decisions can reflect the reality of a workforce with differing job positions, responsibilities, and performance outcomes.
This brings us to one of the principal questions in a pay equity claim: what is “equal work”? To prove a claim under the EPA, an employee must show that the jobs being compared are “substantially equal.” Unlike the EPA, there is no requirement under Title VII that the jobs being compared must be “substantially equal”; instead, Title VII focuses on “similarly situated” employees. As noted in prior blog, at the state level, different variations of these standards proliferate.
In a Pay Discrimination Claim, Who Counts as a “Comparator” Performing “Equal Work” for Greater Pay?
In assessing a pay discrimination claim on the basis of a protected characteristic (like sex, sexual orientation, gender, gender identity or expression, race, color, ethnicity, national orientation, religion, creed, familial status, marital status, veteran status, domestic victim status, disability, and/or age), one commonality between all jurisdictions is the courts’ focus on comparators—individuals who are not members of a plaintiff’s protected class.
For example, in Freyd v. Univ. of Oregon, 990 F.3d 1211 (9th Cir. 2021), the Ninth Circuit considered the case of a female professor who brought an EPA suit against a state university for pay discrimination. The Freyd court held that the plaintiff professor’s four comparators all performed a “common core” of tasks and did “substantially equal work.” Id. at 1220. The court reached this conclusion despite the fact that the comparators performed different research, did not teach the same courses, did not supervise the same doctoral students, did not manage the same centers, and obtained different types of funding. According to the Ninth Circuit, it was the “overall job,” and not “its individual segments,” which formed the basis for comparison. Freyd cautions against drawing overly fine distinctions in deciding whether a plaintiff and her comparators perform “substantially equal work.” Id.
In a different, albeit similar, pay discrimination case, the Fifth Circuit considered the question of comparators, but reached a different conclusion under Title VII. As noted above, a pay discrimination plaintiff in a Title VII case must prove, among other things, that other similarly situated employees outside the plaintiff’s protected class were treated more favorably. The Fifth Circuit held that the comparators cited by the plaintiff-professor did not share plaintiff’s research responsibilities, section assignments, or historical performances, and held that plaintiff could not establish a case of sex discrimination under Title VII. Saketkoo v. Administrators of Tulane Educ. Fund, 31 F.4th 990, 999 (5th Cir. 2022).
Even when courts are analyzing the same pay discrimination statute, the courts take different approaches to the comparator analysis. For example, in contrast to the Ninth Circuit’s focus in Freyd on a “common core” of tasks and an employee’s “overall job” under the EPA, the Fourth Circuit recently held that, in making a finding of “substantially equal work” under the EPA, the “[s]imilarity of work is not enough.” Polak v. Virginia Dep’t of Env’t Quality, 57 F.4th 426, 430 (4th Cir. 2023). Rather, according to the Fourth Circuit, the proffered “comparator [needs] to have performed work ‘virtually identical’ (or the apparent synonym, ‘substantially equal’) to the plaintiff’s in skill, effort, and responsibility.” Id. (emphasis in original).
Polak considered the case of a female coastal planner who worked for a state environmental agency. While the plaintiff and her male comparator (also a coastal planner) were both members of the same team, worked closely together, and collaborated on issues of planning, grant progress, and program performance, the Fourth Circuit concluded that only “the general description of their work was similar.” Id. at 430. Like the plaintiff and her comparators in Freyd, the plaintiff and her comparator in Polak had different responsibilities involving different projects. The Fourth Circuit made several observations. First, plaintiff’s and her proposed comparator’s background, experience, and the subject matter for which they were tasked differed. Second, the Polak court reasoned that “Polak could not have full comparative knowledge of both [her comparator’s] job and hers, as they each performed their work simultaneously in different contexts and on distinct projects to which each were assigned.” Id. at 431 (emphasis added). As a result, the Fourth Circuit held that plaintiff and her comparator did not perform “equal work”, but acknowledged that they did perform “similar work.” Importantly, the Polak court noted “the differences in the actual worked performed and the level of complexity involved were significant enough that their work cannot be fairly described as ‘substantially equal’ or ‘virtually identical,’ as required to establish a claim under the Equal Pay Act.” Id. at 432 (emphasis in original). Unlike the Ninth Circuit, a “common core of tasks” is not enough to meet the “substantially equal standard” in the Fourth Circuit.
Similar to the Fourth Circuit in Polak, the Tenth Circuit recently held that the equal work requirement of the EPA is “not to be construed broadly.” Ferroni v. Teamsters, Chauffeurs & Warehousemen Local No. 222, 297 F.3d 1146, 1149 (10th Cir. 2002). According to the Tenth Circuit, “[l]ike or comparable work does not satisfy this standard, and it is not sufficient that some aspects of the two jobs were the same.” Id.
What Are Some Defenses to Pay Discrimination Claims?
Recent pay equity cases have focused on the relative job experience of plaintiffs with their purported comparators:
- In a recent Tenth Circuit decision, the court dismissed the plaintiff’s EPA and Title VII claims because the plaintiff was a first-year physician and her comparators had at least seven years’ or more experience. Nazinitsky v. INTEGRIS Baptist Med. Ctr., Inc., 852 F. App’x 365, 368 (10th Cir. 2021).
- The Eighth Circuit recently dismissed a professor’s pay discrimination claims for similar reasons. Schottel v. Nebraska State Coll. Sys., 42 F.4th976 (8th Cir. 2022). There, the comparator had five years’ experience teaching, and ten years’ experience as a case worker and case manager at a nearby correctional institute. In contrast, plaintiff had no teaching experience and only three years’ relevant professional experience as a probation officer. Id. at 982.
- In another case, the Eighth Circuit dismissed another pay discrimination claim under Iowa state law involving a cleaner for a building maintenance company who was not offered a position in the special services department. Mayorga v. Marsden Bldg. Maint. LLC, 55 F.4th 1155 (8th Cir. 2022). The court held that the pay differential was due to differences in experience. One male comparator operated the relevant machinery for the special services position in a previous special services position with another company. Another male comparator had over a decade of experience in cleaning services and special services combined. In contrast, plaintiff had only ever worked in general cleaning services. Id. at 1161.
Are There Alternatives?
Another recent case focused on a more formalized and proactive way to ensure pay equity—the practice of internal equity. Korty v. Indiana Univ. Health, Inc., No. 4:21-CV-33-PPS, 2022 WL 17830485 (N.D. Ind. Dec. 21, 2022). There, the court considered the practice of assessing new hires’ compensation rates against incumbent employees’ pay rates to ensure that current and new employees in the same job code have consistent rates of pay. In Korty, the employees who hired a new nurse compared the pay rates of ten other clinical nurse quality coordinators in other job locations. The court held that this practice of internal equity was “a sex-neutral basis for coming up with [the plaintiff’s] salary.” Id. at *6. As such, any differential in pay was not attributable to sex.
The Korty court also held that an employee’s prior salary is also a valid reason “other than sex” to explain a pay differential. Id. at *5. However, employers should be cautious in relying on prior salary to justify any pay differentials. For example, the Ninth Circuit has held that “prior salary alone or in combination with other factors cannot justify a wage differential” because, otherwise, employers could “capitalize on the persistence of the wage gap and perpetuate that gap ad infinitum.” Rizo v. Yovino, 887 F.3d 453 (9th Cir. 2018). The opinion was vacated on unrelated grounds, see Yovino v. Rizo, 139 S.Ct. 706 (2019), but sheds a light on how some courts will view an employee’s prior salary in disputes over pay differentials.
As is evidence from the discussion above, the differences between laws and jurisdictions create a complicated pay equity patchwork for employers to navigate. Employers should consult with experienced counsel to avoid any pitfalls in making compensation decisions and proactively assessing compensation to ensure proper comparators and appropriate justifications depending on the jurisdiction.
Click Here for the Original Article
Colorado privacy law effective July 1; key lessons from the final rules
The Colorado Privacy Act (C.R.S. 6-1-1301, et seq.) (CPA) comes into effect on 1 July 2023. Earlier this year, the Colorado Attorney General promulgated final rules for implementing the CPA (4 CCR 904-3) (the “Rules“). The Rules provide insight as to how the Attorney General may interpret and enforce the CPA. In this alert, we highlight several key aspects of the CPA and the Rules to help businesses focus their compliance efforts.
Background
The CPA is one of the many new state comprehensive privacy laws that have come on the heels of the California Consumer Privacy Act (CCPA). Virginia’s law was effective on 1 January of this year; Connecticut’s law also becomes effective on 1 July. Six other states have enacted similar consumer privacy laws which are slated to come into effect over the coming months and years.
Per our previous alert, the CPA applies to controllers and processors that either (i) control or process personal data of 100,000 or more Colorado consumers during a calendar year; or (ii) control or process data of at least 25,000 Colorado consumer and derive revenue or receive discounts from the sale of personal data. Under the CPA, “personal data” is information that is linked or reasonably linkable to an identifiable individual. It does not include de-identified data or publicly available information. The CPA does not apply to employment or business to business (B2B) data.
In depth
The CPA follows a similar regulatory framework as other US state consumer privacy laws. However, there are certain unique features of the Colorado law that may present compliance challenges for businesses, as detailed below.
- Loyalty Programs
Loyalty programs, which can offer businesses a way to strengthen customer relationships, have attracted increased federal and state regulatory scrutiny in recent years. The Rules do not require specific opt-in consent before a business may enroll a consumer in a loyalty program; however, a consumer’s participation must be voluntary. The Rules mandate particular disclosures that are different than those in the CCPA. Under CPA, the business must provide to consumers:
- a) categories of personal or sensitive data collected under the loyalty program that will be sold or processed for targeted advertising
- b) categories of third parties that will receive such data
- c) list of loyalty program partners and the benefits provided by each partner
- d) an explanation of why a consumer’s request to delete their personal data makes it impossible to provide a loyalty program benefit, if applicable
- e) an explanation of why sensitive data is required to provide a loyalty program benefit, if applicable
Additionally, if a controller’s ability to provide the loyalty program benefit is impacted by a consumer’s exercising of their data rights, the controller should inform the consumer of this impact at least 24 hours before discontinuing the benefit.
- Consent
The Rules also clarify certain requirements under the CPA for obtaining a consumer’s consent to process personal data. Per the Rules, consent that was obtained prior to 1 July 2023, will remain valid as long as the consent was validly obtained through the consumer’s clear, affirmative action, it was freely given, specific, and informed, and it represents the consumer’s unambiguous agreement. If not, or if the purpose for processing has changed or changes in the future or if there has been no interaction with the consumer in the past 24 months, the controller must seek new consent.
The Rules also permit a controller to seek new consent later in cases where a consumer opts out, subject to certain limitations (Rule 7.05). If a controller seeks consent after the consumer has opted out, the consent may not be obtained by methods that cause “consent fatigue” such as interface-dominating cookie banners, high frequency requests, cookie walls, or pop-ups. A controller may proactively send a consumer a link to provide consent if it reasonably believes that the consumer wants to opt back in, Similarly, if a consumer attempts to use a product or service that is inconsistent with their previous opt-out request, the controller may request new consent.
- Data Subject Requests
Under the CPA, consumers have the right to confirm if a controller is collecting their personal data, to access their personal data, to download and remove personal data from a platform in a format that allows the transfer to another controller, and to correct and delete personal data. Consumers also have the right to opt out of the sale of their personal data, the use of their personal data for targeted advertising, and certain types of profiling.
The Rules provide clarifications on how controllers should receive and respond to requests. Under the Rules, a controller may provide a single method for consumers to exercise rights under the CPA and other state laws, but the platform must indicate clearly which rights are available to Colorado consumers (Rule 4.02(C)). The Rules also require a controller’s privacy notice to include a list of data rights available to Colorado consumers (Rule 6.03(A)(3)).
- Data Protection Assessments
The CPA also requires controllers to conduct a data protection assessment when data processing “presents a heightened risk of harm” to consumers. The Rules provide detailed instructions on the assessments, including the expectation that all relevant internal and external stakeholders be involved (Rule 8.03).
Per the Rules, assessments must include: a summary of the processing activity; categories of personal data being processed; the context of the processing, including a description of the controller-consumer relationship; operational elements of the processing; the core purposes of the processing; the risks to the controller, consumers and other stakeholders, and measures the controller will employ to mitigate such risks; relevant internal and external stakeholders involved in the data protection assessment; and any audits conducted as part of the assessment. If the processing involves profiling, additional information should be included in the assessment (Rule 9.06).
Key Takeaways
The Rules confirm that, although the CPA shares a common overall framework with the CCPA and other recent consumer privacy laws, business should review their privacy programs carefully to ensure compliance with the new Colorado law. The US privacy landscape is already complex, and new laws like the CPA demonstrate that companies must find ways to leverage existing compliance resources and adapt to each law’s specific requirements.
Click Here for the Original Article
INTERNATIONAL DEVELOPMENTS
UK and U.S. Announce Commitment to “Data Bridge”
On June 8, 2023, the United Kingdom and the United States announced they reached a commitment in principle to establish the UK Extension to the Data Privacy Framework, which will create a “data bridge” between the two countries. U.S. companies approved to join the framework would be able to receive UK personal data under the new data bridge.
According to the UK government, the data bridge would remove the “burden” of putting in place “costly contract clauses . . . to ensure protection and privacy standards are maintained.” The announcement states that the key pillars underpinning the commitment are “strengthening the rights and safeguards of UK individuals, ensuring robust and reliable data flows, and reducing burdens on business.” It also provides that further “technical work” will be required in the coming months before determining whether the data bridge will be established.
Click Here for the Original Article
EU CJEU confirms broad right of access to personal data under GDPR but protects employee privacy
The Court of Justice of the European Union (CJEU) published its decision in the case of J.M. v Pankki S (Case C‑579/21) on 22 June 2023.
The case concerns the interpretation of Art. 15 GDPR, which grants data subjects the right to obtain access to their personal data and information about the processing of those data from the controller. The case was referred by a Finnish administrative court, which asked several questions about the scope and applicability of the data subject access right in relation to a request made by a former employee and customer of a bank, who wanted to know who accessed his customer data, when and for what purpose.
Background of the case
J.M., a former employee and customer of Pankki S, a Finnish bank, requested access to his customer data, which had been accessed by the bank’s staff on several occasions in 2013. The data subject access request was submitted in May 2018, under GDPR. J.M. wanted to know the identity of the staff members who accessed his data, the dates and purposes of the access and the log data generated by the access. The bank refused to disclose the identity of the staff members, arguing that it was their personal data and that the access was lawful and justified by the bank’s activities. J.M. challenged the bank’s decision before the Finnish supervisory authority, which rejected the appeal, and then before the Administrative Court of Eastern Finland, which referred several questions to the CJEU for a preliminary ruling.
The CJEU decision
The CJEU largely followed the opinion of the Advocate General (AG), with some exceptions mentioned below. The CJEU ruled that:
- 15 GDPR applies to a request for access to personal data that were processed before the GDPR became applicable, as long as the request was made after that date;
- 15(1) GDPR grants the data subject a broad right of access to information about the processing of his or her personal data, including the dates and purposes of the processing operations, in order to make it possible for the data subject to verify the lawfulness of the processing and to exercise the rights conferred by the GDPR. In reaching this conclusion, the CJEU referred to its recent decisions of 4 May 2023 in Österreichische Datenschutzbehörde and CRIF, C‑487/21 (summarised in our blog here) and of 12 January 2023 in Österreichische Post (Information regarding the recipients of personal data), C‑154/21 (discussed in our blog here);
- The CJEU agreed with the opinion of the AG that Art. 15(1) GDPR generally does not grant the data subject a right of access to information about the identity of the controller’s employees who carried out the processing operations under the authority and in accordance with the instructions of the controller. However, the CJEU reached a different conclusion: it held that such a right may exist if this information is essential for the data subject to effectively exercise the rights under the GDPR and provided that the rights and freedoms of the employees are taken into account;
- In the event of a conflict between, on the one hand, the exercise of a right of access and, on the other hand, the rights or freedoms of others, a balance will have to be struck. The CJEU states that, wherever possible, the means of communicating personal data which does not infringe the rights or freedoms of others must be chosen; and
- The fact that the controller is a bank (and acts within the framework of a regulated activity) and that the data subject was also an employee of the controller has no bearing, in principle, on the scope of the right of access under Art.15 GDPR.
The CJEU also confirmed that the employees of the controller cannot be regarded as “recipients” of data within the meaning of the GDPR, when they process the data under the authority of the controller and in accordance with its instructions.
The press release is available here and the decision here.
Click Here for the Original Article
MISCELLANEOUS DEVELOPMENTS
Requirement to show citizenship or permanent residency held to be discriminatory
A Canadian appeals court has held that human rights law requires all those with legal permission to work to be treated equally at the point of hiring, and that imposing an additional requirement of citizenship or permanent residency will amount to unlawful discrimination.
In a recent decision, the Ontario Court of Appeal unanimously held that human rights law prevents employers from requiring employees to hold Canadian citizenship or permanent residence rather than another kind of work permission.
Mr Haseeb was an international student who applied to Imperial Oil for an entry-level project engineer position. Imperial offered Mr Haseeb the position on condition that he provide proof of Canadian citizenship or permanent residency. Mr Haseeb was not a permanent resident, but was going to be eligible to work full-time anywhere in Canada for up to three years with a Post-Graduate Work Permit (‘PGWP’). After Mr Haseeb revealed to Imperial that he was not a permanent resident, they revoked the job offer. Mr Haseeb then filed a human rights application alleging that the permanent residency requirement discriminated against him on grounds of citizenship, contrary to the Ontario Human Rights Code (the ‘Code’).
In 2018, the Tribunal hearing Mr Haseeb’s initial claim decided that it was discriminatory for employers to require job applicants to prove their Canadian citizenship or permanent residency status to be eligible to work, and ordered Imperial Oil to pay more than CAD 100,000 in damages. In judicial review proceedings, the Divisional Court of Ontario reversed that decision, holding that permanent residency was not a protected ground encompassed within the term citizenship. Mr Haseeb appealed this ruling.
The Court of Appeal held that Imperial Oil’s requirement for proof of Canadian citizenship or permanent residency was discrimination because it excluded a group of non-Canadian citizens who were legally entitled to work full-time anywhere in Canada.
The Court of Appeal said that the purpose behind including ‘citizenship’ as a protected ground under the Code was to ensure that individuals eligible to work in Canada under federal immigration law were treated equally. In doing so, the Court of Appeal noted that the Code has an exception that would allow an employer to impose a Canadian citizenship requirement where this is required or authorised by law.
The Court of Appeal also considered the purposes of federal immigration law, holding that the purpose of the PGWP program is to allow individuals to obtain Canadian work experience so they might subsequently apply for permanent residency. The Court of Appeal ultimately held that interpreting the Code in a manner that would allow employers to discriminate against those not permitted, at a particular point in time, to work in Canada permanently would be contrary to the purposes of federal immigration law and programs like the PGWP.
Employers may wish to review their hiring policies in light of this decision and should be cognizant of potential discrimination claims based on citizenship or immigration status.
Click Here for the Original Article
Artificial Intelligence Briefing: EU Parliament Approves AI Act
The European Parliament approves a revised draft of the EU AI Act, Senate Majority Leader Chuck Schumer lays out plans for groundbreaking AI legislation in the U.S., and the FTC issues a warning that companies who ignore consumers’ data rights do so “at their own peril.” We explore these developments and other regulatory updates in the latest briefing.
Regulatory and Legislative Developments
- EU Parliament Approves the AI Act. On June 14, 2023, the European Parliament voted to adopt a compromise position on the draft text of the proposed EU AI Act. The revised draft now includes extensive obligations on developers of foundation models — AI trained on large data sets to accomplish a wide range of downstream tasks. The revised draft also expands the categories of prohibited AI significantly, including prohibitions on indiscriminate scraping of biometric data from social media to create facial recognition databases, and adds further categories of high-risk systems, including systems that influence voters in political campaigns. Penalties are also increased significantly to up to 7% of global revenue. The draft text will now be subject to a final set of trilogue negotiations during the latter half of 2023.
- Senator Majority Leader Lays Out Approach for AI Legislation. On June 21, Senate Majority Leader Chuck Schumer (D-NY) laid out his proposed approach for enacting groundbreaking AI legislation. It starts with a basic framework that encourages safe innovation and calls for security, accountability, protection of our democratic foundations and (especially) explainability. It also includes a new legislative process for developing policies to implement the framework, starting this fall with a series of AI insight forums.
- President Biden Addresses AI Opportunities and Risks. On June 20, President Biden met with tech leaders in a closed-door session to discuss what he described as AI’s “enormous promise and its risks.” Top administration officials are reportedly meeting multiple times each week to develop executive orders and other actions that the federal government can take with respect to artificial intelligence. Next month, Vice President Harris will meet with civil rights leaders, consumer protection groups and others as part of the administration’s ongoing efforts.
- FTC Issues Warning. In a June 13 blog post, the Federal Trade Commission warned that it “will hold companies accountable for how they obtain, retain, and use the consumer data that powers their algorithms.” The post also says that “companies that ignore consumers’ rights to control their data do so at their peril.”
- State AGs Weigh In.On June 12, 23 state attorneys general submitted a comment to the National Telecommunications and Information Administration (NTIA) calling for independent standards for transparency, testing, assessments, and audits in AI governance. They also called for certain measures to be adopted into federal law, including a human review of AI-driven decisions in certain high-risk use cases, aligning AI governance standards with state privacy rights, and concurrent enforcement powers between the federal government and state attorneys general. The letter was signed by the attorneys general of Arizona, Arkansas, California, Colorado, Connecticut, Delaware, the District of Columbia, Illinois, Maine, Minnesota, Nevada, New Jersey, New York, North Carolina, Ohio, Oklahoma, Pennsylvania, South Carolina, South Dakota, the U.S. Virgin Islands, Tennessee, Vermont, and Virginia. The NTIA is within the U.S. Department of Commerce and advises the President on telecommunications and information policy.
- Global Insurance Regulators Provide Update. Last week’s IAIS Global Seminar in Seattle featured a panel focused on AI, where Rhode Island Superintendent Beth Dwyer (who chairs the NAIC’s Big Data and AI Working Group) said, “We feel very strongly that it is our duty to avoid as many unintended consequences to consumers as possible, while still allowing the benefits.” Immediately following the Global Seminar on June 16, the Steering Committee of the EU-U.S. Insurance Dialogue Project provided an update on its work and future priorities, including with respect to AI. (The Dialogue Project began in 2012 as a means of enhancing cooperation between EU and U.S. insurance regulators.) The summary reporty released in connection with the Dialogue Project does a nice job of describing efforts on both sides of the Atlantic.
- Employers, Beware! NYC AI Audit Law Will Soon Be Effective. On July 5, 2023, New York City will begin enforcing Local Law 144, which regulates the use of AI-driven tools in certain employment decisions. Local Law 144 applies to all employers and employment agencies that hire employees who reside in New York City, regardless of the employer’s location. Under the law, employers will be liable if they fail to comply with the law’s requirements, which include commissioning and publishing the results of an annual independent bias audit; providing notice of the use of the AI-driven hiring tools to candidates and employees; and providing an alternative selection process or reasonable accommodation to those who request it.
Click Here for the Original Article
New York to Increase Wage Protections for Executive, Administrative, and Professional Employees
Seyfarth Synopsis: The New York State Legislature has passed a bill that increases the earnings threshold for executive, administrative, and professional employees to file a complaint with the New York Department of Labor for owed wages under Article 6 of the New York Labor Law.
Article 6 of the New York Labor Law, the State’s wage theft statute, sets forth various requirements relating to the payment of wages. Among other things, the statute prohibits employers from unlawfully withholding wages from employees employed in the State. If an employer violates Article 6, aggrieved employees may pursue a private action against the employer or file a complaint with the New York Department of Labor to recover the owed wages.
However, the DOL previously rejected wage theft claims from executive, administrative, or professional employees making more than $900 per week. Employees above this earnings threshold were solely limited to commencing a private action in civil court.
The bill, which will become effective 180 days after Governor Kathy Hochul’s expected signature, seeks to correct the “DOL’s inflexible approach to Article 6 enforcement” by increasing the weekly wage threshold for those employed in an executive, administrative, or professional capacity. The bill increases the earning threshold from $900 to $1,300 per week. As such, executive, administrative, and professional employees making $1,300 or less per week will no longer be confined to commencing a lawsuit in civil court to recover owed wages. The DOL will have the authority to receive complaints, commence an investigation, and recover owed wages for such employees.
Importantly, the Bill does not alter the salary thresholds for classifying employees as exempt under the New York Labor Law. The bill pertains only to the requirements for filing a complaint with the DOL for owed wages. For more information about the minimum salary requirements for exempt status under the Labor Law, please see here.
In addition to increasing the weekly wage threshold, the bill makes clear that the following provisions under Article 6 will now apply to executive, administrative, and professional employees making less than $1,300 per week:
- Labor Law § 192 (cash payment of wages) – Requires employers to obtain advance employee consent for payment by direct deposit.
- Labor Law § 198-c (benefits or wage supplements) – Requires employers to timely pay all amounts and benefits owed to employees under company policy and sets forth penalties for an employer’s non-compliance.
Employers with operations in New York should consider revisiting their wage payment practices with respect to executive, administrative, and professional employees to ensure compliance with applicable requirements.
Click Here for the Original Article
Is an employer allowed to require genetic testing?
An overview of the most important provisions concerning genetic tests in the employment relationship.
Adjustments to the rules on human genetic testing
The revised provisions of the Federal Act on Human Genetic Testing (HGTA) as well as the ordinance and subsidiary decrees have been in force since 1 December 2022. This has led to various changes (cf. the other magazine articles on this topic).
The amendments regarding genetic testing in employment are not substantial. Employers may continue to demand the performance of genetic tests and the disclosure of already existing genetic data only in certain cases. In practice, these possibilities have seemingly not yet been used.
The permissible scope of employers is determined on the one hand by the HGTA and on the other hand by the Code of Obligations (CO).
The requirements of the CO and HGTA regarding genetic tests in employment relationships
Starting point: pursuant to Art. 328b CO, genetic information and data may only be collected and handled in the context of employment negotiations or during an employment relationship to the extent that they relate to the suitability for the specific employment relationship.[1]
The HGTA incorporates this requirement of Art. 328b CO. According to this, genetic tests initiated in connection with an employment relationship may only be carried out to clarify medical properties that are relevant at the workplace (Art. 38 HGTA). However, the HGTA restricts the scope of application of genetic tests to the extent that employers are prohibited from requesting that genetic tests be carried out outside the medical field, as well as from asking for or exploiting genetic data that is not medically relevant (Art. 37 HGTA).
Moreover, the HGTA fundamentally prohibits presymptomatic genetic tests as well as the disclosure or utilisation of genetic data which originate from earlier presymptomatic genetic tests. Presymptomatic test are tests whose purpose is to identify predisposition to disease before clinical symptoms emerge. Exceptionally, presymptomatic genetic tests are permitted for the prevention of occupational diseases and accidents if specific conditions are fulfilled (Art. 40 HGTA).
What applies in the event of a breach of the requirements under the CO and HGTA?
If the employer processes genetic data that does not meet the requirements of the CO and HGTA, he is basically acting in a way that violates personal rights. In this case, the employee can take civil action against the employer. The employee has contractual, personal and data law options. Non-compliance with the provisions of the HGTA is also subject to criminal law. Intentional offences are punishable by custodial sentence of up to three years or a monetary penalty (Art. 56 para. 1 HGTA).